Hide GPS Location in mobile phone from trackers COVID-19
Autorius: ghost Šaltinis: https://www.social-searcher.co... 2020-05-27 18:28:00, skaitė 2506, komentavo 2
In previous article we talk about Hide GPS Location in mobile phone and get good response and you all like that one. And i got too many comments on Part 2 so i decide to teach you guys more about GPS Spoofing. Let’s Start:
Imagine agreeing to meet a friend at a cafe you’ve never been to before. You are already 20min late, but you’re confident your GPS will get you there. Suddenly, however, your GPS shows that you are in a different country and it’s the year 2038. What just happened? Someone spoofed your GPS.
What is GPS spoofing?
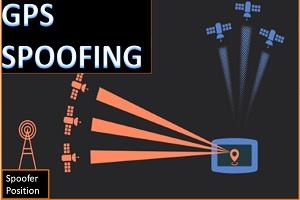
GPS spoofing is an attack whose main goal is to override a GPS-enabled device’s original location. To do so, the attacker uses a radio transmitter that broadcasts a fake GPS signal and interferes with GPS receivers nearby. As a result, those devices display fake GPS locations. Smartphone owners can spoof their GPS by downloading third-party apps, which fool other apps into thinking that the device isn’t at its original location.
The Global Navigation Satellite System (GNSS), which GPS (the Global Positioning System) is a part of, is also used to sync the date and time across devices around the world. Thus, if your device is spoofed, it might also suddenly show that you have traveled to the future or back in time.
How GPS spoofing works
GPS spoofing attacks used to be very expensive, mostly relegating them to use in warfare. Why? Because GPS spoofing can fake ships’, airplanes’ and vehicles’ locations to confuse the enemy. While it is still used for this purpose, location spoofing has since become accessible to ordinary hackers. All they need is a portable radio signal transmitter with open-source software, which can be bought for under $300.
The GPS finds your location by using satellites orbiting the Earth. They continuously transmit radio signals that your GPS-enabled device uses to triangulate your location.
The problem is that by the time these radio signals reach your device, they become fairly weak. This means that any transmitter with a stronger signal can cause a denial of service attack. It simply overpowers them and makes your device show whatever location it wants. Why is that a problem? Because any GPS device can be affected.
What is GPS spoofing used for?
- Warfare. It can change the perceived location of ships, planes, and other vehicles. For example, a hacker could make a fake aircraft appear on airplane’s GPS so that a pilot would think there’s another aircraft approaching them when there isn’t.
- Taxi trips. Taxi drivers can use it to fake their location to earn more money or standing (even though the trip wasn’t completed), or it could be used to disguise their location for criminal activities. This can be a huge security risk for passengers.
- Construction disruption. GPS navigators are used to control some construction machinery. Just imagine the fatal effect a ton of bricks would have if it was dumped in the wrong place.
- Geofencing. GPS systems are used to track delivery drivers and deliveries. Long-distance truck drivers usually have GPS-powered geofencing systems that lock the truck until it reaches its destination. Malicious actors can spoof the truck’s location to steal its cargo.
- Apps. Some apps can help you spoof your smartphone’s location. This might be convenient if you play games like Pokemon Go (which has some privacy issues). However, these location spoofers will make all your apps think that you are somewhere else. You might not want to use them if you need reliable directions.
Can you protect yourself?
Anti-GPS spoofing technology is being developed, but it may not be available (or necessary) for the average user any time soon. However, if you run a business, there are a few more things you should do to protect yourself:
- Have a backup system ready if you see a sudden change in GPS coordinates and time. For example, rubidium or cesium clocks can be used as backup timing systems until the original connection is restored.
- If you need to track drivers, deliveries, planes or ships from an office building, you may want to obscure your building’s antennas. Fake transmissions will usually come from closer than a satellite signal would. It would also come from the ground up. Obscuring your antennas will protect your building from receiving fake signals.
- If you run an app or a business that uses GPS locations, you could use machine learning and other analytics to cross-check suspicious data.
How to spoof your location on Android
- Download a GPS spoofing app
- Enable Developer options
- Select mock location app
- Spoof your location
- Enjoy your media
1. Download a GPS spoofing app
First, head to the Play Store and search for GPS spoofing apps. I recommend Fake GPS location primarily because it’s one of the highest rated GPS spoofing apps available. You can choose whichever one you like though.
2. Enable Developer options
Next, if you haven’t already done so, enable Developer options on your phone. To do this, jump into your settings menu by pulling down the notification shade and tapping on the gear icon. From there, scroll down to the bottom of the list and select the System option.
From there, choose About phone and rapidly tap on Build number. After, you will need to verify your lockscreen security, and then Developer options will be unlocked. To locate it, hit the back button once and select the new Develop options item.
3. Select mock location app
Now that you’re inside the Developer options menu, first make sure the toggle at the top of the list is turned on. Next, locate the Select mock location app option. Choose Fake GPS location or whichever app you installed on your device.
4. Spoof your location
With all of the above step taken care of, open the Fake GPS location app or whichever app you downloaded for this process. For Fake GPS location, you can either place your pin in a general location (such as a state or two away from you) or search for a specific address. After hit the “go” button and you should be spoofing your location.
5. Enjoy your media
If everything worked as planned, you should now be able to hop into your favorite media apps such as YouTube TV, MLB.TV, ABC, or so on and watch your desired event. Unfortunately, this isn’t going to be a full proof solution as some apps can detect when the mock location setting is in use and will block playback.
